What is Decentralized VPN? Elevating Online Privacy
Embark on a digital odyssey with us as we unravel the essence of “What is Decentralized VPN” Beyond the technology, this exploration becomes a proactive stride toward safeguarding your online privacy in the face of increasing threats. Join us in understanding how decentralized VPNs redefine the landscape, offering not just protection but a pathway to reclaiming your digital freedom.
What is Decentralized VPN?
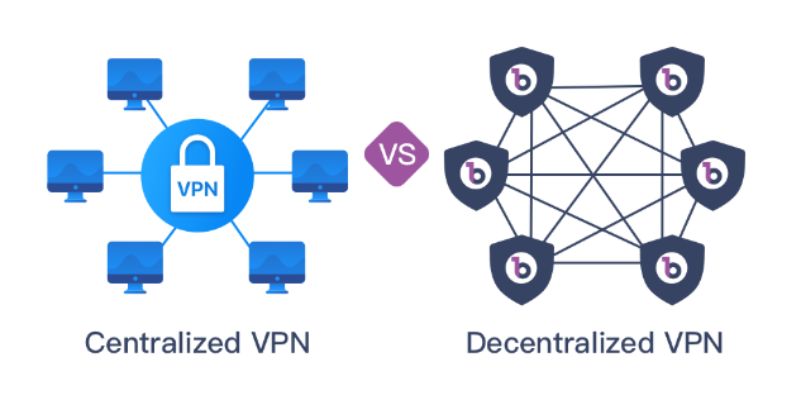
Decentralized VPNs mark a significant departure from traditional VPNs by eliminating centralized authority over server networks. Instead, they operate on a peer-to-peer model where numerous users contribute their unused network traffic, creating an independent network of nodes.
Rather than relying on servers owned by VPN providers, users become integral parts of this network. The architecture of decentralized VPNs is typically supported by blockchain technology, offering a transparent and secure governance framework.
Contributing to the decentralized VPN network can earn users rewards without the need for specialized hardware. Compensation often comes in the form of unique tokens and cryptocurrency, encouraging network expansion and active user engagement.
How does a decentralized VPN work?
Decentralized VPNs provide an opportunity for individuals to function as both users and service providers, aiming to establish a peer-to-peer network that eliminates the necessity for a central point of control.
Users can integrate their nodes through devices such as laptops or mini-computers like Raspberry Pi. These services create VPN tunnels to redirect data, utilizing open-source VPN protocols commonly found in traditional services. IP addresses are allocated to clients based on routing rules, nodes, and tunnels, allowing users to choose their preferred locations, as is the case with regular and decentralized VPNs.
The utilization of decentralized VPNs mirrors that of traditional Virtual Private Networks. Providers of dVPNs typically offer software for installation by interested users. Once set up, users can access a list of available nodes, and during the connection process, they may encounter additional features such as selecting DNS providers or activating a kill switch.
The pricing models for decentralized VPNs vary. Some providers may offer subscription plans, where users pay fixed fees for unlimited access, while others adopt an alternative approach, requiring users to pay only for the bandwidth they consume.
Advantages and disadvantages of using decentralized VPNs
Advantages of using decentralized VPNs
1. Enhanced Privacy and Security:
– Decentralized VPNs distribute network control, reducing the risk of a single point of failure or vulnerability.
– The peer-to-peer nature can make it harder for malicious actors to exploit centralized servers.
2. Censorship Resistance:
Decentralized VPNs may be more resistant to censorship, as there is no central authority that can be targeted or pressured to restrict access.
3. User Empowerment:
Users can actively participate in the network by becoming both users and providers, fostering a sense of empowerment and community involvement.
4. Reduced Dependence on Centralized Providers:
Decentralized VPNs eliminate reliance on a single provider, mitigating the risk of data logging or surveillance by a central authority.
5. Flexibility and Customization:
Users have more control over their VPN experience, from choosing nodes to configuring routing rules, providing a more tailored and flexible solution.
Disadvantages of using decentralized VPNs
1. Technical Complexity:
Setting up and managing decentralized VPNs can be more technically challenging compared to using traditional VPN services, potentially limiting accessibility for non-technical users.
2.Variable Performance:
The performance of decentralized VPNs may vary depending on the number and quality of nodes available. In some cases, it might be slower than centralized alternatives.
3. Limited Server Locations:
Decentralized VPNs may have a more limited selection of server locations compared to large, centralized VPN providers, potentially affecting the user’s ability to access content from specific regions.
4. Potential for Abuse:
The peer-to-peer nature of decentralized VPNs can attract users with malicious intent, leading to potential abuse of the network for illegal activities.
5. Incomplete Anonymity:
While decentralized VPNs offer increased privacy, they may not guarantee complete anonymity, especially if users’ IP addresses can be traced through the peer-to-peer connections.
6. Development and Support Challenges:
Decentralized VPNs might face challenges in terms of ongoing development, updates, and user support, as these networks rely on community participation.
In summary, the choice between centralized and decentralized VPNs depends on individual priorities and preferences, balancing factors like privacy, security, technical expertise, and ease of use.
Differences between centralized and decentralized VPNs
Centralized VPNs and decentralized VPNs differ in several key aspects, ranging from their architecture to their implications for privacy and security. Here are some notable differences:
1. Architecture:
Centralized VPNs: Operate on a traditional client-server model, where users connect to a central server or a network of servers controlled by a single entity.
Decentralized VPNs: Utilize a peer-to-peer architecture, distributing control and functions across multiple nodes, with users acting as both consumers and providers.
2. Control and Authority:
Centralized VPNs: Have a central authority or provider that manages and controls the entire network. Users rely on this central entity for connectivity and services.
Decentralized VPNs: Lack a single central authority, as users contribute to the network by sharing their resources (such as bandwidth) and collectively participating in routing.
3. Privacy and Security:
Centralized VPNs: Users trust the central provider to maintain privacy and security. However, this reliance on a single entity raises concerns about data logging and potential vulnerabilities.
Decentralized VPNs: Aim to enhance privacy by eliminating a central point of control, reducing the risk of surveillance or data logging. Users have more control over their data.
4. Censorship Resistance:
Centralized VPNs: May be more susceptible to censorship, as authorities can target and block access to the central servers or IP ranges controlled by the VPN provider.
Decentralized VPNs: Tend to be more resistant to censorship, as there is no single point of control that can be easily targeted. Users connect directly to each other, making it challenging to block the entire network.
5. User Participation:
Centralized VPNs: Users typically play a passive role, connecting to servers provided by the central entity without actively contributing to the network infrastructure.
Decentralized VPNs: Encourage user participation by allowing them to become both users and providers, contributing resources (such as bandwidth) to the network.
6. Ease of Use:
Centralized VPNs: Generally offer a more straightforward setup process and user experience, making them accessible to a broader range of users, including those with limited technical knowledge.
Decentralized VPNs: May require more technical expertise for setup and configuration, potentially limiting accessibility for non-technical users.
7. Server Locations:
Centralized VPNs: Tend to offer a wide range of server locations across the globe, providing users with options for geographically diverse connections.
Decentralized VPNs: May have a more limited selection of server locations, depending on the availability of nodes within the decentralized network.
Ultimately, the choice between centralized and decentralized VPNs depends on individual preferences, priorities, and the specific use case. Users may weigh factors such as privacy, security, ease of use, and resistance to censorship when deciding which type of VPN best suits their needs.
A regular VPN vs. dVPN: which is better?
We commend the introduction of innovative approaches to enhance individuals’ online privacy and anonymity. While decentralized VPNs hold promise, their effectiveness is contingent on proper implementation. Just like any VPN-type service, adherence to stringent ethical, security, and reliability standards is crucial.
Whether opting for traditional VPNs or decentralized alternatives, service providers must maintain transparency regarding their operations. In both scenarios, encountering deceitful or subpar products is a possibility. Fortunately, reliable providers can offer the advantages of traffic encryption and IP masking.
If you seek a conventional VPN with a no-logs policy, look no further. Atlas VPN ensures the non-collection of users’ original IP addresses or details about their online activities. For example, we are unable to discern the specific actions of clients while they browse the internet through our centralized servers.
Furthermore, the use of cryptocurrency for payments is not uncommon among traditional VPNs. Atlas VPN is among the providers that accept cryptocurrencies such as Bitcoin or Ethereum.
Conclusion
In summary, exploring the concept of “What is Decentralized VPN” not only opens a new door for enhancing online privacy but also presents challenges in terms of transparency and reliability. In today’s world of online threats, understanding “What is Decentralized VPN” is not just a technological exploration but a journey towards reclaiming our digital autonomy and safeguarding our online privacy rights. Follow Solution of Blockchain to update more knowledge about technology.