Category Archives: Blog
How does blockchain in digital identity work today?
In today’s digital age, our identities are constantly at risk. But what if you could...
What is sharding technology in blockchain?
Is your blockchain struggling to keep up? Discover how sharding technology is revolutionizing scalability and...
What is Web3 ecosystem? What are the next generation of the internet?
Imagine an internet where you own your data, control your digital identity, and interact directly...
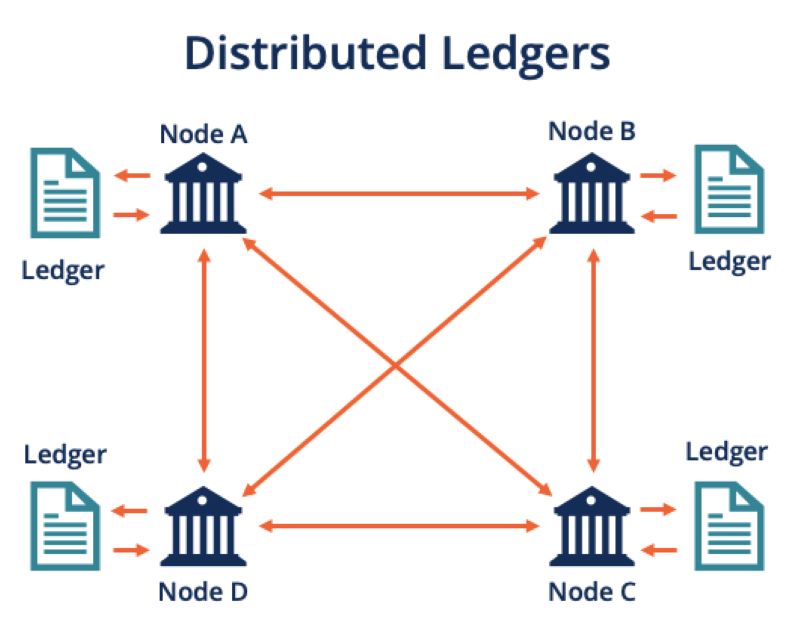
What is distributed ledger technology (DLT)? How Distributed Ledger Technology Works?
Tired of intermediaries, data breaches, and slow transactions? Discover the revolutionary potential of Distributed Ledger...
Introducing Directed Acyclic Graph (DAG) & Use case
Tired of tangled processes? Discover the power of Directed Acyclic Graphs (DAGs) to streamline complex...
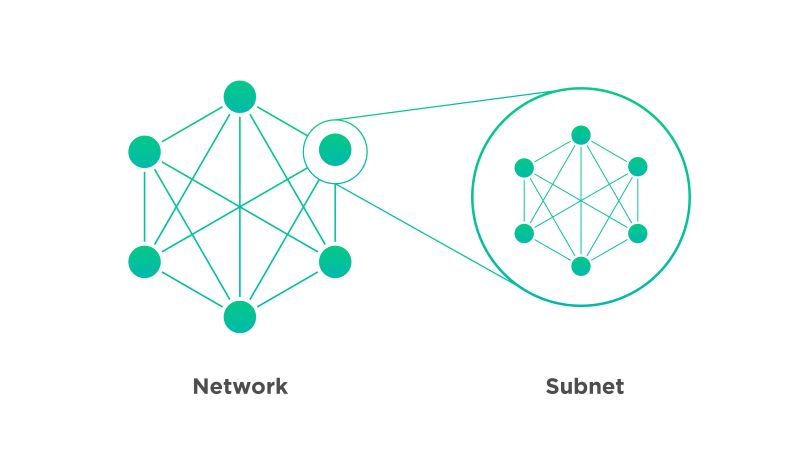
What is U2U Subnet? How does U2U Subnet work?
U2U Subnet is a groundbreaking Layer-2 scaling solution designed to address the limitations of traditional...
Protecting Personal Privacy in the Digital Age: Concerns and Challenges
In today’s digital age, personal privacy has become one of the most important and prominent...