Elevate your Blockchain security best practices for business and individuals! Dive into strategies to fortify digital assets against threats. From smart contract audits to continuous monitoring, safeguard your ecosystem. Stay ahead, ensure integrity, unlock power!
What are the Principles for Blockchain Security?
Understanding the core principles of blockchain security is paramount for safeguarding your digital assets. Delve into the world of blockchain technology to uncover effective strategies for ensuring security. By grasping the fundamentals of blockchain, you gain insights into its decentralized nature and cryptographic underpinnings. Immutability, transaction transparency, decentralized access, and cryptographic security form the bedrock of blockchain security.
These principles ensure that transactions are tamper-proof and transparent, with detailed audit trails for monitoring. However, it’s essential to acknowledge that blockchain security relies on user responsibility. Vulnerabilities such as phishing attacks and smart contract errors can compromise security, emphasizing the need for proactive measures to mitigate risks.
Existing State of Blockchain Security
Blockchain security stands as a vital pillar in risk management, encompassing cybersecurity frameworks, secure coding, and rigorous testing methodologies. Its core mission is to shield against online fraud, breaches, and various attacks.
Cryptography, consensus, and decentralization emerge as key security principles in blockchain. Yet, vulnerabilities persist, with the financial impact of security breaches mounting. The projected $20 billion global blockchain market by 2024 only intensifies the allure for attackers.
Recent security breaches underscore the imperative of blockchain security. Notably, the DAO hack’s $60 million loss and breaches in blockchain bridges highlight the evolving threat landscape. With increased adoption of blockchain solutions, prioritizing blockchain security becomes paramount.
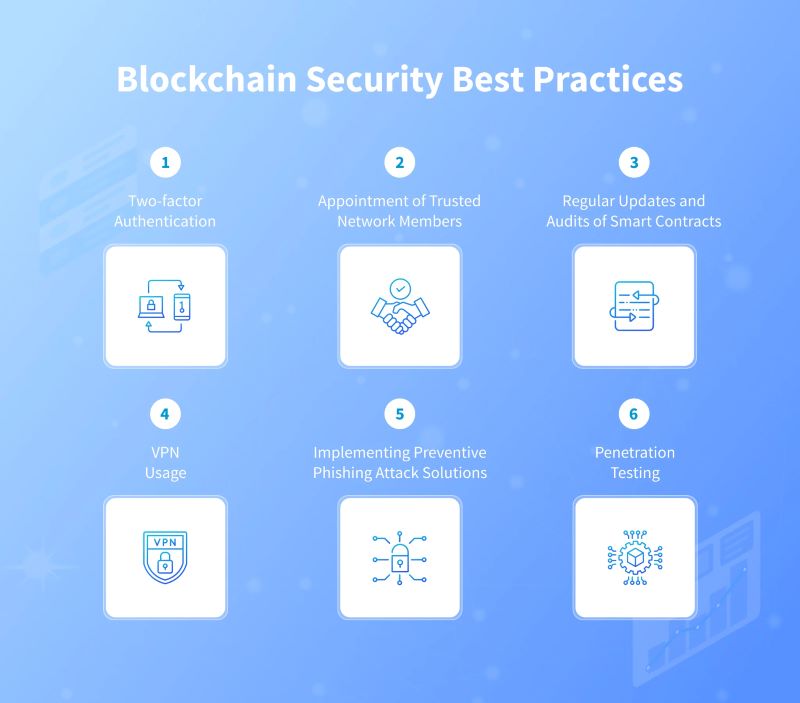
What are the Blockchain security best practices for business and individuals
The burgeoning adoption of blockchain by businesses underscores its transformative potential. However, security concerns loom large, posing challenges to trust establishment. Here are key best practices to fortify blockchain security:
Anticipate Future Security Challenges
Businesses must recognize the inherent cryptographic security of blockchain, while also acknowledging potential vulnerabilities. Avoiding the inclusion of personally identifiable information (PII) mitigates risks associated with potential advancements like quantum computing.
Minimize Large File Usage
To optimize efficiency and security, businesses should refrain from storing large files directly on blockchain networks. Instead, employ pointers or links to external storage platforms like Google Cloud or AWS. Additionally, utilize hashing algorithms to verify file integrity and detect alterations.
Embrace Permissioned Blockchains
For enhanced privacy and control, opt for permissioned blockchains, which restrict data access and transactions to authorized parties. Platforms like Hyperledger offer tailored solutions, ensuring sensitive data remains protected within defined boundaries.
Consider Scalability and Performance
Evaluate blockchain networks based on scalability, performance, and security requirements. Navigate the blockchain trilemma by selecting networks that strike a balance between these elements, prioritizing security without sacrificing scalability or performance.
Establish Governance Structures
Prevent security lapses by establishing robust governance frameworks prior to blockchain implementation. Define clear procedures for user management, decision-making processes, and conflict resolution, ensuring efficient management of blockchain networks.
By adhering to these best practices, businesses can fortify their blockchain implementations, mitigating security risks and unlocking the full potential of this transformative technology.
How Can Businesses Develop Secure Blockchain Solutions?
Ensuring blockchain security demands a proactive approach to solution development. By adhering to best practices, businesses can effectively address vulnerabilities and fortify their blockchain solutions. Here’s how:
Embrace Security-by-Design:
Adopt a security-centric mindset from the outset of solution development. Define and enforce endorsement agreements based on business contracts to establish clear security parameters.
Implement Identity and Access Management:
Employ robust identity and access management controls to regulate data access within blockchain networks. Secure storage of identity keys and leverage industry-standard tokens like OAuth, SAML2, and OIDC for user authentication, authorization, and verification.
Employ Privileged Access Management (PAM):
Enhance security by implementing PAM solutions to safeguard blockchain ledger entries. Employ strong cryptographic key management tools to protect sensitive data.
Ensure API Security:
Adhere to API security best practices to secure API-based transactions. Implement multi-factor authentication to bolster authentication processes.
Safeguard Sensitive Information:
Utilize data classification and privacy-preserving technologies to protect sensitive data. Leverage hardware security modules and effective security incident and event management to bolster overall security posture.
Patch Security Loopholes:
Regularly patch security vulnerabilities to preempt data breaches and mitigate risks. Enforce compliance and security controls alongside standard Transport Layer Security (TLS) for both external and internal communications.
Is Blockchain Penetration Testing Useful for Blockchain Security?
Yes, blockchain penetration testing is a valuable tool for enhancing blockchain security. It serves as a proactive security assessment process designed to identify and address vulnerabilities within a blockchain solution. Here’s how businesses can benefit from blockchain penetration testing:
Understanding Blockchain Architecture:
By conducting penetration testing, businesses gain insights into their blockchain architecture and identify potential attack surfaces. This understanding enables them to proactively assess and mitigate security risks.
Identifying Security Flaws:
Penetration testing helps uncover security loopholes, misconfigurations, and vulnerabilities within the blockchain solution. By identifying these flaws early on, businesses can take corrective measures to strengthen their security posture.
Testing Compliance
Penetration testing also assesses the compliance of the blockchain solution with security standards and regulations. This ensures that the solution meets industry-specific security requirements and regulatory mandates.
Comprehensive Testing Approach
Through various testing techniques such as API security testing, functional testing, and network vulnerability assessment, penetration testing provides a comprehensive evaluation of the blockchain solution’s security. This thorough approach helps in uncovering both known and unknown security issues.
Exploitation Verification
The exploitation phase of penetration testing validates the impact of security weaknesses and vulnerabilities discovered during testing. By simulating real-world attack scenarios, businesses can assess the potential risks posed by these vulnerabilities and prioritize remediation efforts accordingly.
In conclusion, implementing robust blockchain security best practices is paramount to safeguarding your digital assets against evolving threats. By conducting smart contract audits, continuous monitoring, and staying proactive, you can ensure the integrity and resilience of your blockchain ecosystem. Take action now to fortify your defenses and unlock the full potential of blockchain technology. Ready to elevate your security? Contact Solution of Blockchain today to learn more and fortify your blockchain solutions.